Overview of the Best Incident Management Systems
Incidents can occur in any business. The stability and long-term success of a company directly depend on its ability to respond effectively to such situations. That’s why incident management systems are a crucial investment in the future of any organization. In this article, we will explore the leading solutions available on the market and introduce a custom-built system developed for one of Evrone’s clients.
Incident management is critical for any business, yet off-the-shelf solutions don’t always fit unique workflows. In this article, I explore the best existing incident management systems and share how Evrone built a custom solution for a leading tech company.
What Is an Incident?
An incident is any event or situation that disrupts normal operations, services, or processes—or has the potential to do so. Incidents can occur in various industries, including IT, manufacturing, security, and healthcare.
An Incident Management System (IMS) is a tool or set of processes designed for incident identification and logging, analysis, resolution, and prevention within an organization.
Why Is Incident Management Important?
System failures, process errors, or security threats can lead to significant losses in terms of time, resources, and reputation. Ignoring incidents often results in recurring issues, increased costs, and reduced service quality. A structured incident management practice not only minimizes the impact of incidents but also allows companies to learn from them, enhancing business resilience.
Moreover, incident response automation ensures compliance with regulatory requirements, optimizes resource allocation, and improves communication between teams.
Key Benefits of an Incident Management System
- Minimizing Downtime: Faster response and resolution reduce system downtime.
- Enhanced Service Quality: A structured incident management process ensures more stable and reliable operations.
- Regulatory Compliance: Many industries mandate incident management software to meet compliance standards (e.g., ISO 27001, ITIL).
- Resource Optimization: Efficiently allocates resources for problem resolution.
- Improved Communication: A centralized incident management system streamlines information flow across teams.
- Continuous Improvement: Analyzing past incidents helps organizations refine internal processes and mitigate future risks.
Essential Features of an Incident Management System
An effective incident management system should provide end-to-end incident lifecycle management—from detection to resolution and analysis. Below are the core features:
1. Incident Identification and Logging
The system should capture all relevant data, including incident description, timestamp, location, affected systems or processes. Data entry can be manual (via templates) or automated through integration with monitoring and observability tools.
2. Classification and Prioritization
For efficient handling, incidents must be categorized based on type—such as hardware failure, software bug, or security breach. The system should assign priority levels based on urgency and impact. A tagging system can simplify filtering and searching incidents.
3. Assignment and Escalation
The system should allow for quick assignment to the relevant teams or specialists and support automatic escalation if an issue is unresolved within a set timeframe. A well-defined incident response process ensures that all stakeholders understand their roles and responsibilities.
4. Incident Response and Resolution
The platform should provide real-time tracking of resolution progress, including task management for responsible employees. Built-in chat tools and notifications enable smooth communication. Additionally, predefined incident response automation workflows can be used for common issues, speeding up resolution.
5. Monitoring and Incident Management
- Real-time alerts: Notifications via email, messaging apps, or SMS.
- Integration with monitoring systems for immediate detection.
- Customizable dashboards for tracking ongoing and resolved incidents.
6. Post-Incident Analysis and Reporting
- Historical incident tracking to improve future responses.
- Customizable reports for analyzing incident frequency, resolution times, and patterns.
- Root cause analysis (RCA) tools to prevent recurring issues.
7. Integration and Scalability
A risk management system must adapt to growing business needs and integrate seamlessly with ITSM platforms, CRM, ERP, and other monitoring and observability tools.
8. Automation Capabilities
- Automated incident routing based on type and priority.
- Predefined remediation workflows for rapid response.
- Automatic server restarts and issue resolution triggers.
9. Access Control and Security
- Role-based access control ensures data confidentiality.
- Audit logs track all system actions for accountability.
10. Mobile Accessibility
- Mobile applications or web interfaces allow for incident management on the go.
- Push notifications help alert on-call staff immediately.
Comparing Top Incident Management Software
The market offers a range of incident management tools, from global leaders to regional solutions. Below is a comparison of leading platforms based on their key features, pricing, and support.
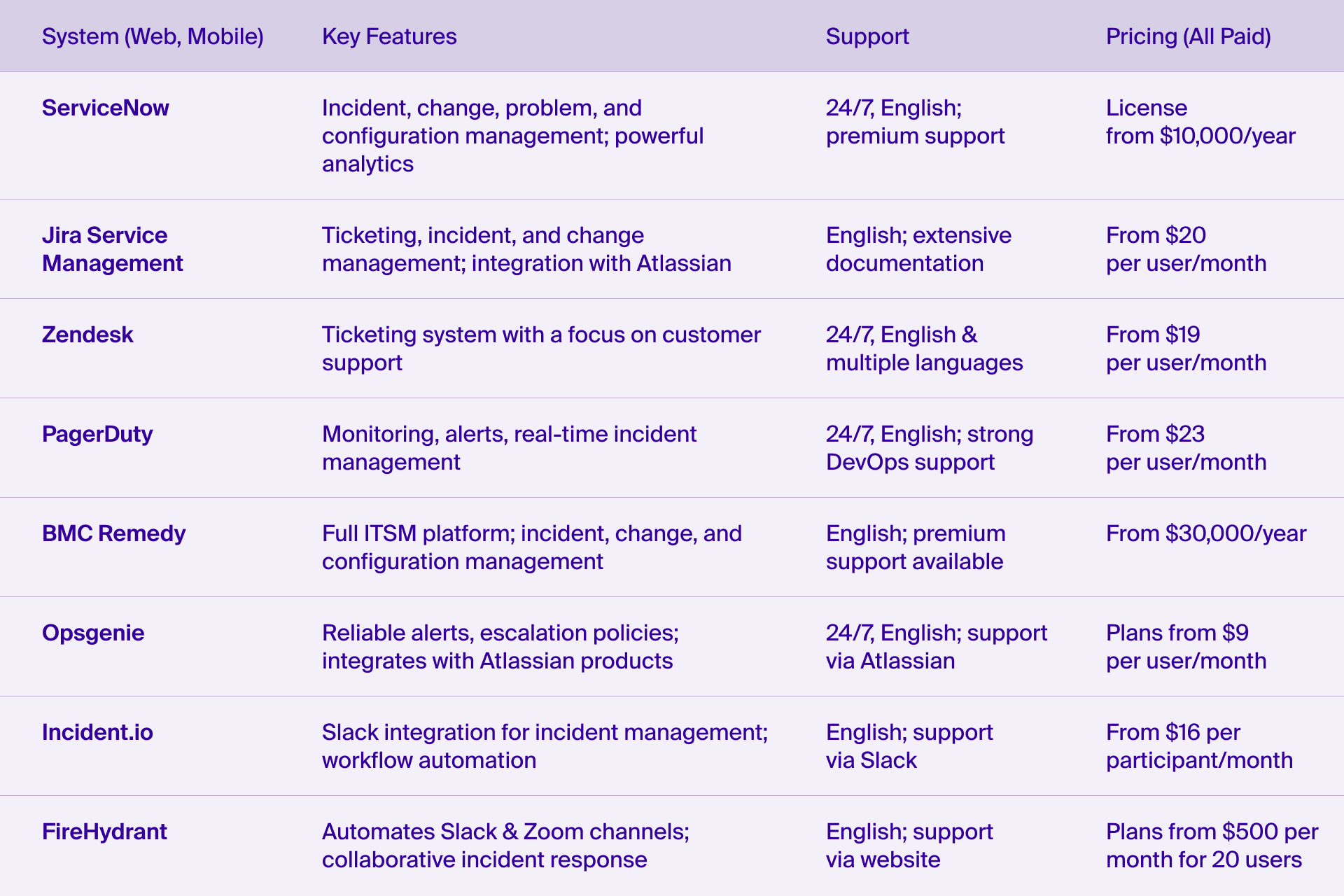
Off-the-shelf solutions provide many benefits but may not always meet a company’s unique needs. Factors like limited customization, high costs, or complex implementation can make custom-built incident management software a better choice.
Many pre-built solutions are designed for generic use cases and may not support specific business processes. Custom development allows for tailored features, optimized workflows, and full integration with existing infrastructure.
Building a Custom Incident Management System
To illustrate the benefits of custom-built solutions, let's look at an Evrone project for a client—a major Russian technology company that we can't name because of the NDA. The concept for this risk and vulnerability management system was fully designed by the client, while our developers helped bring the idea to life.
General Overview
The client had been collecting knowledge base data for a long time, and the first version of their incident tracking platform was built using Jira. However, over time, Jira's capabilities became insufficient.
The new system allows managers to:
- Log incidents
- Automatically notify participants through multiple communication channels
- Maintain an incident log
- Validate hypotheses
- Compile reports after incidents are resolved
The platform aggregates service metrics, on-call staff availability, and historical changes within the last 12 hours that could have contributed to an incident. It also highlights affected user scenarios.
Alongside graphs and analytics dashboards, the system includes tracers, logs, and a structured storage system.
Telemetry System
The company had an extensive telemetry system in place to monitor all services. Each service had preset thresholds that would trigger alerts in case of potential failures.
A 24/7 on-call team was responsible for system uptime, ensuring that in case of an incident, there was always someone available to respond. The primary goal of the new system was to centralize all incident management processes into a single platform.
System Components & Technology Stack
The incident management system consists of the following modules:
- Core Service – manages incidents and aggregates all related information
- Work Planning Service – a calendar-based system that tracks scheduled activities that could potentially cause issues
- Platform Event Log – an event aggregator that shows incident managers which services were deployed or rolled back at the time of an outage
- Legacy On-Call Management Service – provides on-call personnel information to quickly assign them to incident response teams
Tech Stack
- Go – primary programming language
- Python – used for the on-call management service
- Custom communication protocol – facilitates interaction between all components
- Fully re-engineered work calendar – ensuring smooth operation in the new cluster
Database Architecture
The legacy services used PostgreSQL, but for the core service, the client required a more scalable and flexible solution.
The incident structure follows a hierarchical model:
- Incident
- On-call engineer
- Participants
- Attachments
- Messenger thread
Since this structure fits well with MongoDB, we chose it as the primary database.
Database Logic & Algorithms
Our specialists reworked queries with complex logic to integrate with the incident response system’s metrics notifications. The challenge was to ensure that alert statuses changed dynamically based on metric values.
We replaced the old alert processing method with a new query structure. Additionally, we conducted load testing to ensure database stability.
Troubleshooting System
The incident management system contains a large knowledge base that helps incident managers make informed decisions. To enhance usability, we built a troubleshooting system that provides real-time recommendations.
For example, if a service starts lagging, the system generates an alert and simultaneously provides diagnostic insights—such as high latency or a surge in database transactions.
The goal is to:
- Help incident managers quickly assess issues
- Provide relevant insights without overloading users with unnecessary data
Suggestions may include:
- Current system metrics
- Incident logs
- Theoretical knowledge from the internal database
The system assists in decision-making but does not replace human judgment.
Automation & Future Plans
The system is already operational but continues to evolve. The primary focus is on incident response automation.
Initial implementation:
- Incident tracking relied on manual reporting via chats and calls
- Later, metrics, graphs, and release logs were introduced
Next Steps
- Automating incident detection & resolution
- Building an event collection service to detect system irregularities
- Developing microservices for increased security and stability
To enhance security, we split the project into microservices.
Authorization Module
- Handles user access and tracks system activity
- Integrates with the central user management system
- Generates tokens and logs user actions
Different user roles have varying levels of access, ensuring customized permissions within the incident hierarchy.
Towards Autonomous Incident Management
Currently, the system relies on broader ecosystem resources. However, in the event of a major system-wide failure, it may degrade alongside other services.
To prevent this, we are implementing a standalone, autonomous incident management model—ensuring continued functionality even during large-scale outages.
Business Impact
Evrone’s developers continue working on the project alongside the client’s team, scaling and refining the incident management system.
We built the entire codebase from scratch, launched it into production, and it is now actively used in business operations.
This project demonstrates that custom software development can be a superior choice, as no existing platform offers the same level of flexibility and security.
For instance, Atlassian discontinued Jira support in Russia, highlighting the risks of third-party dependency. Companies prioritizing data security and independence are increasingly investing in custom-built solutions.
Conclusion
The market offers numerous solutions for structuring vulnerability management processes and incident response workflows.
- Pre-built solutions are great for companies with standardized operations.
- Custom-built systems provide maximum flexibility, security, and independence.
The choice between an off-the-shelf platform and a custom-built solution depends on budget, time constraints, and business requirements.
If your company prioritizes tailored automation and advanced security, a custom incident management system is the best long-term investment.
Looking for a tailored solution? Evrone specializes in custom incident management software development—contact us to discuss your project!
